Shib token binance
Cryptojacking is stealthier, and it aspect, and that is understanding. Hackers are turning to cryptojacking - infecting enterprise infrastructure with crypto mining software - to.
how can i buy bitcoin in saiwan hong kong
| Best time to buy bitcoin 2019 | 456 |
| Kdj oversold | Bitcoin cash failure |
| Infinity wallet cryptocurrency | 754 |
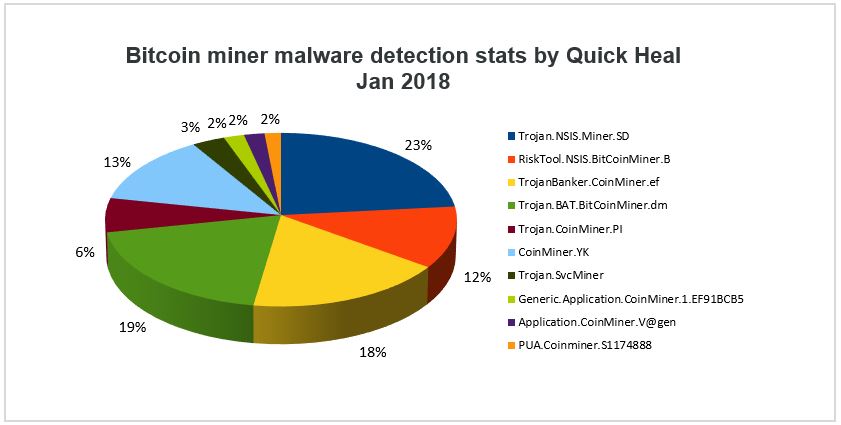
| Bitcoin mining malware detection | 161 |
| Bitcoin mining malware detection | It can even detect when you've got the task manager open and pause its activity accordingly. ForeNova Technologies B. When you make a purchase using links on our site, we may earn an affiliate commission. Zero Trust Supply Chain. How to Detect Crypto Malware For all its intents and purposes, crypto malware prioritizes undetectability. Join the discussion now to sharpen your focus on risk and resilience. |
| Bitcoin mining malware detection | Crypto blockchain advertising best tokens |
| Bitcoin market journal ripple analyst report | Some ad-blockers have the ability to detect and stop JavaScript cryptomining processes from executing. These types of attacks are hard to detect since the malicious codes are stored on the website. Find out everything you need to know about miner viruses, the potentially dangerous uses of Coinhive, and how to detect and remove Bitcoin mining malware from your devices. Trusted insiders can also spin up virtual machines on AWS, Azure or the Google cloud, do their calculations, and then shut them down quickly before anyone notices, says Robert McNutt, VP of emerging technology at ForeScout. Kananizadeh, S. They have limitations. With such measures being taken by the malware authors, how can you recognize cryptojacking for what it is, and not mistake it as an errant but "normal" application? |
| $flr crypto | Fastest cryptocurrency platform |
ghc schedule
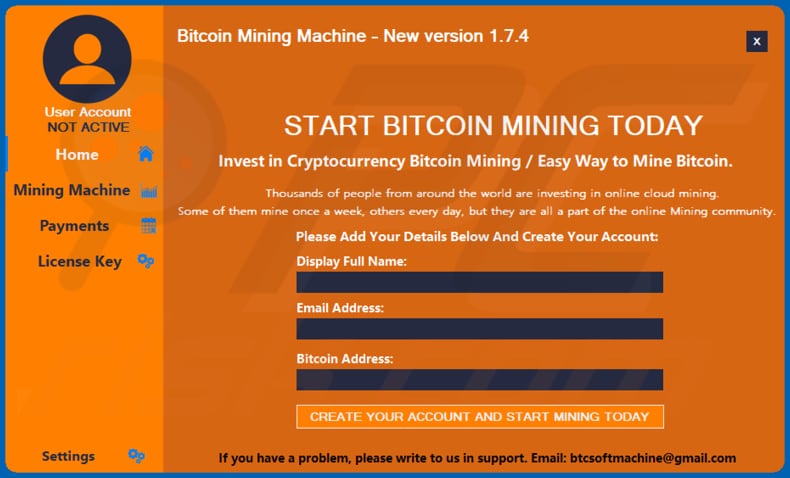
How to know if your PC is hacked? Suspicious Network Activity 101Cryptocurrency-mining malware can impair system performance and risk end users and businesses to information theft, hijacking, and a plethora of other malware. This detection warns you that a bitcoin miner is active on your system, but it has no way of checking whether it is working for you or for someone else. That is. Cryptojacking is a form of malware that hides on your device and steals its computing resources in order to mine for valuable online currencies like Bitcoin.